SecureOvercast is
a global provider of innovative,
sophisticated, rapidly deployable
cybersecurity penetration testing
services. Our penetration tests
model attack scenarios as a means of
testing the end-to-end security
infrastructure, and identifying all
security vulnerabilities.
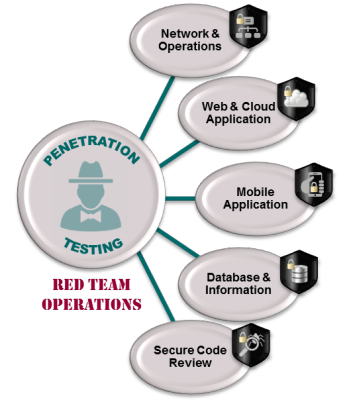
PENETRATION TESTING - RED TEAM OPERATIONS Our penetration testing services are aimed at providing your business with a clear understanding of your security infrastructure's overall effectiveness. Our sophisticated Defense-In-Depth testing methodologies provide you with the real-time state of your security infrastructure. Our penetration tests don’t just identify potential risks - we use the same attacks and methods that hackers do to test your systems, confirm risk and verify the viability and severity of vulnerabilities. We don't just make your security plan look great on paper, we physically determine how effective your security actually is in real-time! |